cyber crime in malaysia
The website of Oahu Transit Services OTS operator of TheBus and TheHandi-Van is once again functioning after being disabled by. Cyber Extortion Cyber extortion known by the rather less interesting name of threatening to damage a computer is just the high-tech variation of old-fashioned extortion.
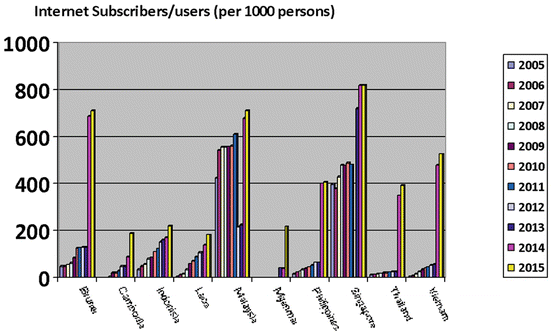
Cybercrime And Cyber Security In Asean Springerlink
The present article aims to get an overview of the cyber-crime as it is defined and revealed by specialized literature international legislation and historical facts and perform an analysis of.
. Yet private and public entities still struggle to secure their systems and adversaries have increased. Different types of high-tech crime may also include elements of low-tech crime and vice versa making cybercrime investigators an indispensable part of modern law enforcement. The relevant authority in charge of the MACCA is the Malaysian Anti-Corruption Commission MACC.
This article is written by Shambhavi Tripathi a 3rd-year student of LLB. On March 17 2021 the FBI released its Internet Crime Report 2020 which stated that American victims reported 42 billion in losses as a result of cybercrime and internet fraud to the FBI last year. This includes online harassments defamation electronic theft and etc This article sets out all legal protections for all internet users in Malaysia be it via computers smartphones or any other internet devices.
Ensuring the security of cyberspace is fundamental to protecting Americas national security and promoting the prosperity of the American people. LGMS is named as one of the Internet of Things IoT key penetration testing vendors in the 2018 IDC Report. Become and expert at cyber prosecution and defence.
Similarly to Singapore Malaysia is also very well prepared in terms of cybersecurity. In 2014 it was once again witnessed that cyber laws all over the world are still lagging behind to deal with the emerging cyber crime trends 3. This is ASCLs advanced course in cyber law.
So far in 2021 one threat has surpassed all others both in increase and in degree of devastation. In 2017 China have adopted a new Cyber Security Law and it main purpose was to increase the cybersecurity and the national security. Please cite any Applicable Laws in your jurisdiction applicable to cybersecurity including laws applicable to the monitoring detection prevention mitigation and management of IncidentsThis may include for example data protection and e-privacy laws intellectual property laws confidentiality laws information security laws and importexport.
Advanced Program in Cyber Law. Chief Inspector Cheung Wai-ho of the cyber security and technology crime bureau said the gang hunted. What is Cyber Crime.
Digital media contain footprints that physical forensic data and the crime scene may not include. Cyber Security Penetration Testing Firm. It further discusses the pros and cons of the IT Act 2000 and changes brought in by the IT Amendment Act 2008.
Voip scam- cross border syndicates. In the mid-year update to the 2021 SonicWall Cyber Threat Report we shine a light on the growing scourge of ransomware. Cyberspace is an integral component of all facets of American life including the countrys economy and defense.
Malware is a type of application that can perform a variety of malicious tasks. In Panjab University Chandigarh. Under the federal Computer Fraud and Abuse Act it is a crime to threaten to damage someones computer in order to extort money information or anything else of value.
Established in 2005 LGMS is accredited with multiple international certifications that makes it a leading cyber security penetration testing and assessment firm in the Asia Pacific region. Share of internet users who experienced cyber crime Malaysia 2016 by type Share of cyber crime incidents within region 4-a Philippines 2019 by type Cyber crime in region 3 Philippines 2019 by type. It is also relevant to all online applications users such as Lazada Facebook.
15 Common Types of Cyber Attacks. The opportunity to learn never stops. Malaysia cybercrime cases year total cases losses rm million 2007 1139 114 2008 1821 129 2009 3863 223 2010 6167 630 2011 6586 805 2012 4738 961 royal malaysia police top 3 number of cases.
Why is this role important. E-commerce fraud- online purchase 2. Why its continued its meteoric rise which ransomware families are most responsible and what regions and industries are most likely to be targeted.
In 2014 emergence of the dark web was marked and cybercrime emerged as an economy model in the dark web. We set out 9 types of cyber offences or activities that can be caught under this legal framework. The article is written by Ramanuj Mukherjee CEO Lawsikho and updated by Pooja Kapur a 5th year law student from Amity Law School Noida and Yash Jain a third-year student of Institute of Law Nirma University.
You are the sleuth in the world of cybersecurity searching computers smartphones cloud data and networks for evidence in the wake of an incidentcrime. Methods of cybercrime detective work are dynamic and constantly improving whether in closed police units or in international cooperation framework. The FBIs Internet Crime Complaint Center claimed that it received an average of more than 2000 complaints per day through 2020.
Well cover everything from global spying think FBI. 21 Applicable Law. It is located in Sepang District SelangorCyberjaya is adjacent to and developed along with Putrajaya Malaysias government seatThis city aspires to be known as the Silicon Valley of Malaysia.
Cybercrime with Cyber laws and security and led to several recommendations for stakeholders. The security team breaks news crafts exclusives and produces a narrative podcast about famousinfamous major hacks. Also learn about the cyber crime laws of many countries including Australia Canada European Union Gulf Cooperation Council Japan Malaysia Singapore UK and USA.
Usually located in countries with lax e-crime laws Bolivia Indonesia and Malaysia are currently very popular they represent safe addresses for goods purchased with stolen financial details to be sent or else safe legitimate bank accounts for money to be transferred into illegally and paid out of legitimately. While there are many different ways that an attacker can infiltrate an IT system most cyber-attacks rely on pretty similar techniques. The article is an introduction to cyber crimes and cyber law and the impact of cyber crimes.
It has been ranked third in the Global Cybersecurity Index 2017. Hong Kong Malaysia police arrest 27 people in Interpol crackdown on romance scam gang. Seven International Cyber Defendants Including Apt 41 Actors Charged in Connection with Computer Intrusion Campaigns Against More Than 100 Victims Globally Caution.
However it has attracted heated. Below are some of the most common types of cyber-attacks. Cyberjaya a portmanteau of cyber and Putrajaya is a city with a science park as the core that forms a key part of the Multimedia Super Corridor in Malaysia.
By Kherk Ying Chew and Eddie Chuah Baker McKenzie Malaysia Domestic bribery private to public 11 Legal framework The key anti-corruption legislation in Malaysia is the Malaysian Anti- Corruption Commission Act 2009 MACCA which came into force on 1 January 2009. The article discusses the concept of cyber crime complaint and how to file a cyber crime complaint both offline and online.

Fraud Continues To Be The Main Cause Of Cybersecurity Incidents In Malaysia

300 Terrifying Cybercrime Cybersecurity Statistics 2022

Cybercrime Goes Mobile Http Infographic Mobile Life Infographic Marketing Mobile Marketing

Cyber Crime Experts Explain The Process Www Asianlaws Org Cyber Law Social Media Super Powers

The Importance Of Reporting Cybercrime Rsm Global
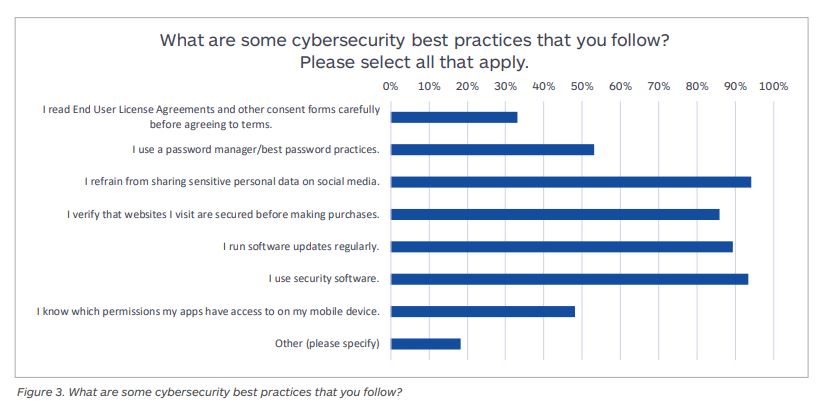
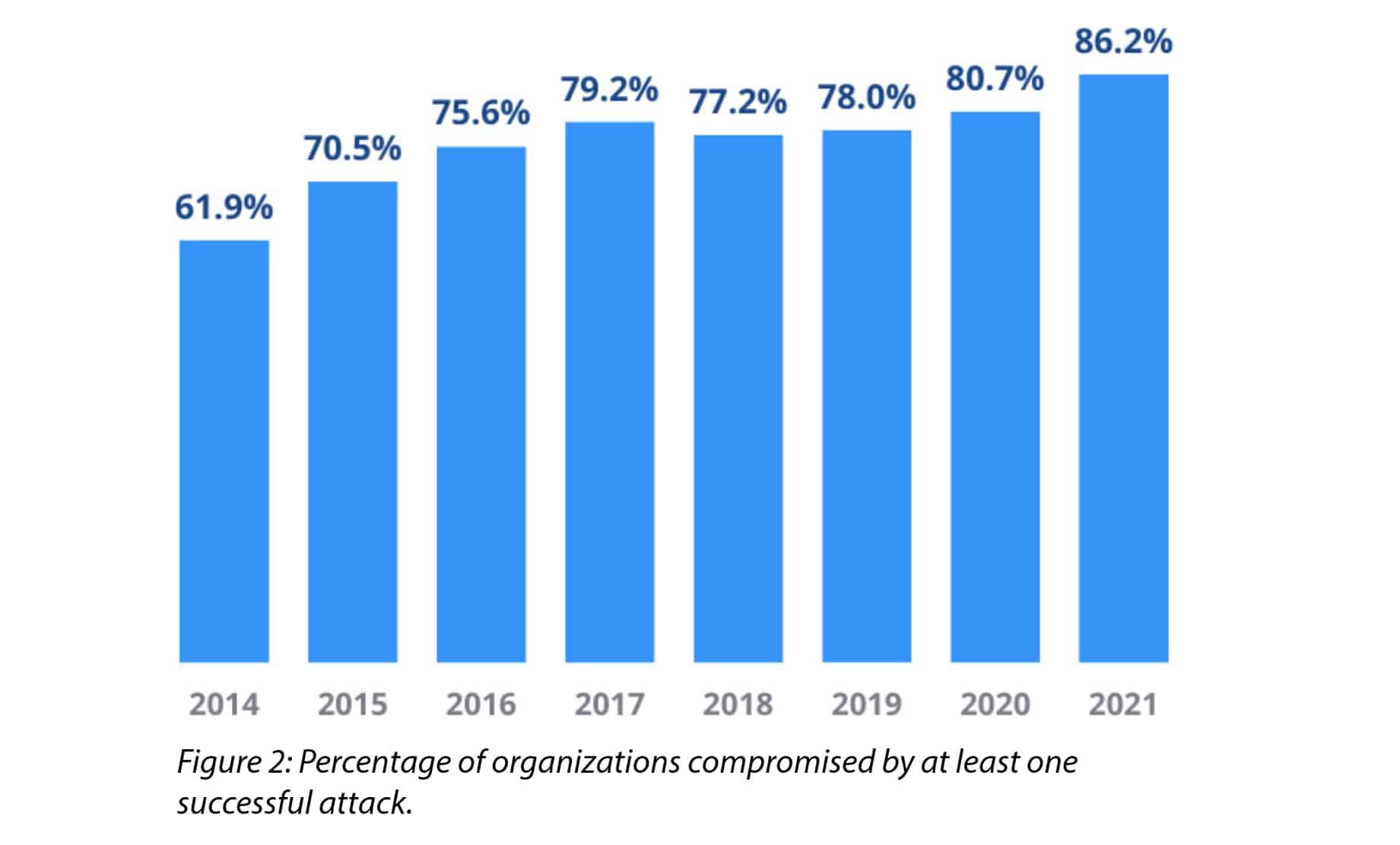
300 Terrifying Cybercrime Cybersecurity Statistics 2022

Why Malaysia Should Amend Its Cyber Security Laws

Rasmussen College Online Safety Infographic Cyber
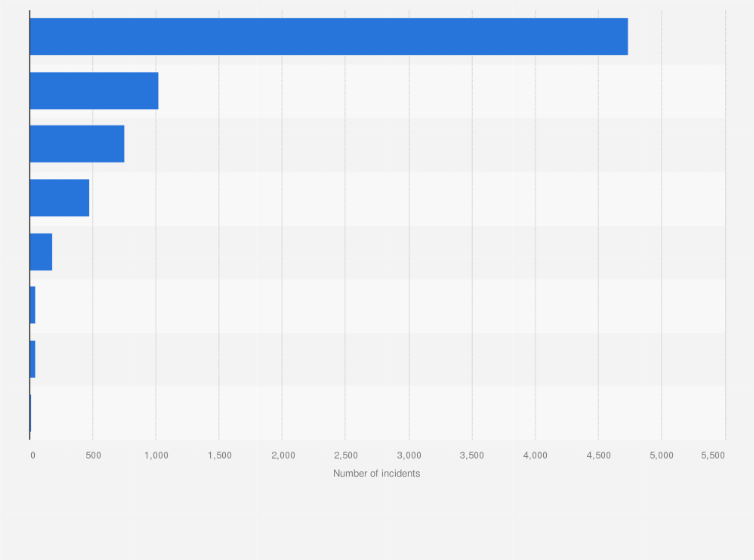
Malaysia Cyber Crime Incidents 2020 Statista

300 Terrifying Cybercrime Cybersecurity Statistics 2022

Malaysia Cyber Crime Incidents 2020 Statista

Pin By Dan Williams On Cyber Security Cyber Security Capital Market Listed Company
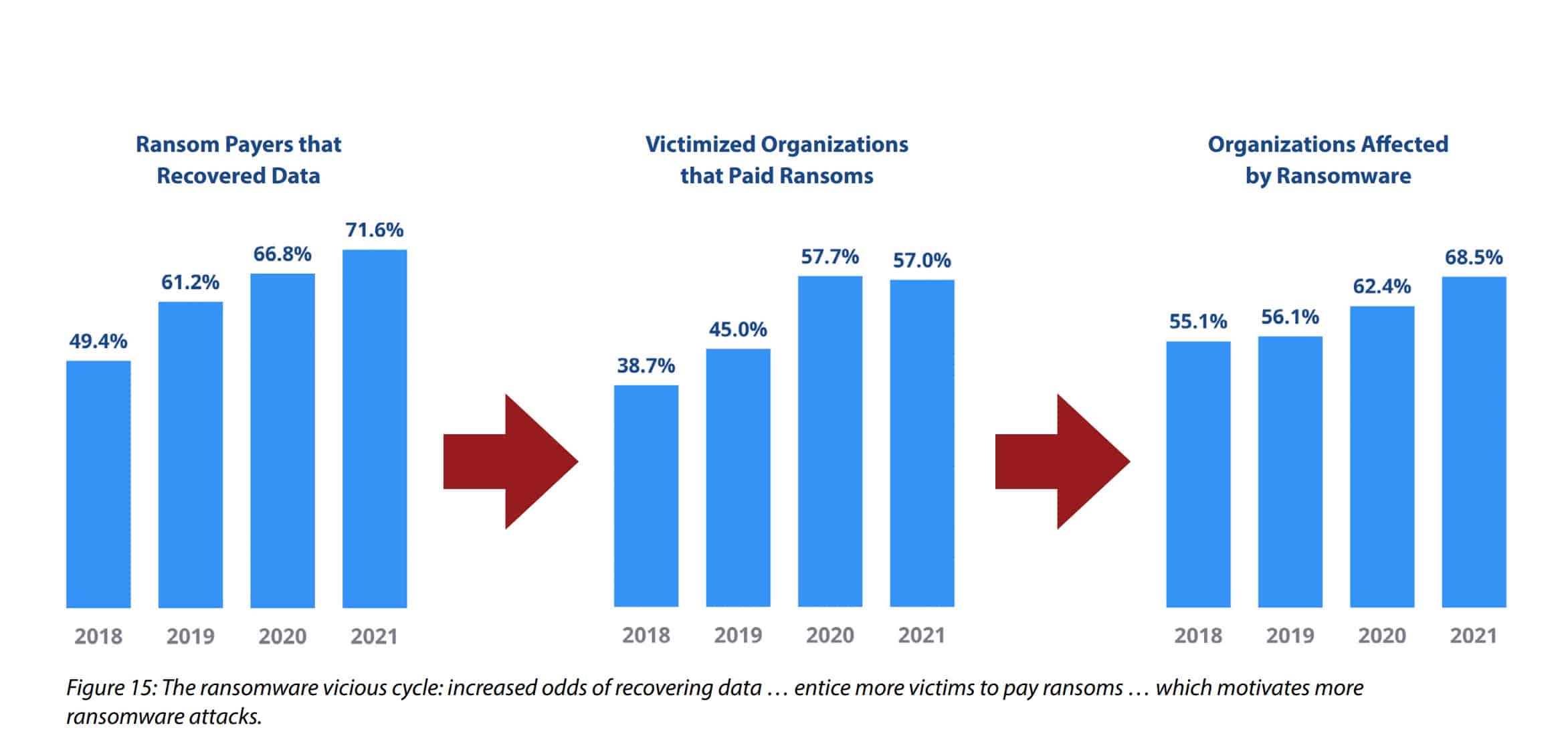
300 Terrifying Cybercrime Cybersecurity Statistics 2022

Which Countries Are Best Prepared For Cybercrime Response

Malaysia Type Of Cyber Attacks On Organizations 2017 Statista

Ascl In Malaysia Www Asianlaws Org Cyber Law Prevention Government

Cyber Crime In Malaysia Rm1 Billion Lost By Conned Victims

Pin By Harineshwary A P Suntaram On Quick Saves In 2021 Cyber Security Computer Crime Identity Fraud

El Perfil De Un Cibercriminal Infografia Infographic Internet Cyber Security Awareness Computer Security Cyber Security